VSRX防火墙安装与部署
本文共 8587 字,大约阅读时间需要 28 分钟。
Juniper vSRX的安装与部署
一、准备工作
- Juniper官网下载15.1的.ova模板的junos
- 一台安装ESXI5.1, 5.5 ,6.0的服务器
- 两台vmx模拟PC测试,一台vsrx防火墙(15.1x49-d170)
二、操作部署
- 使用vSphere Client登录ESXI服务器
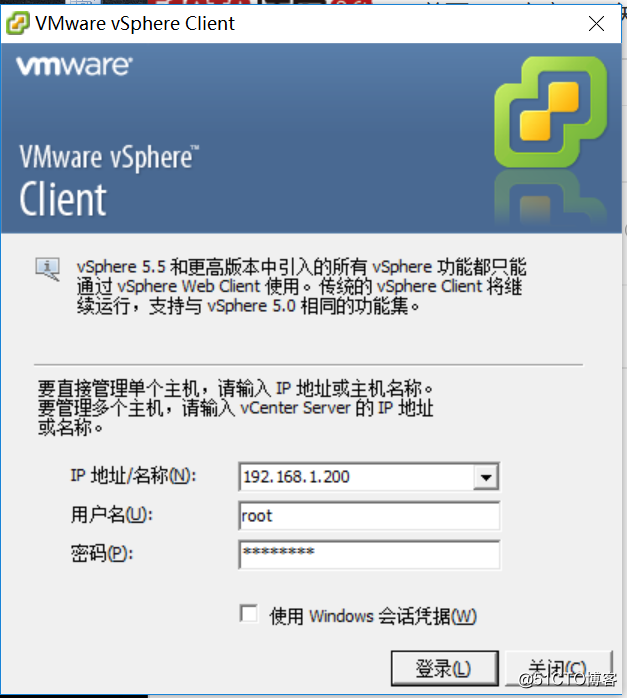
- 在登录的界面中,点击文件部署”OVA模板“
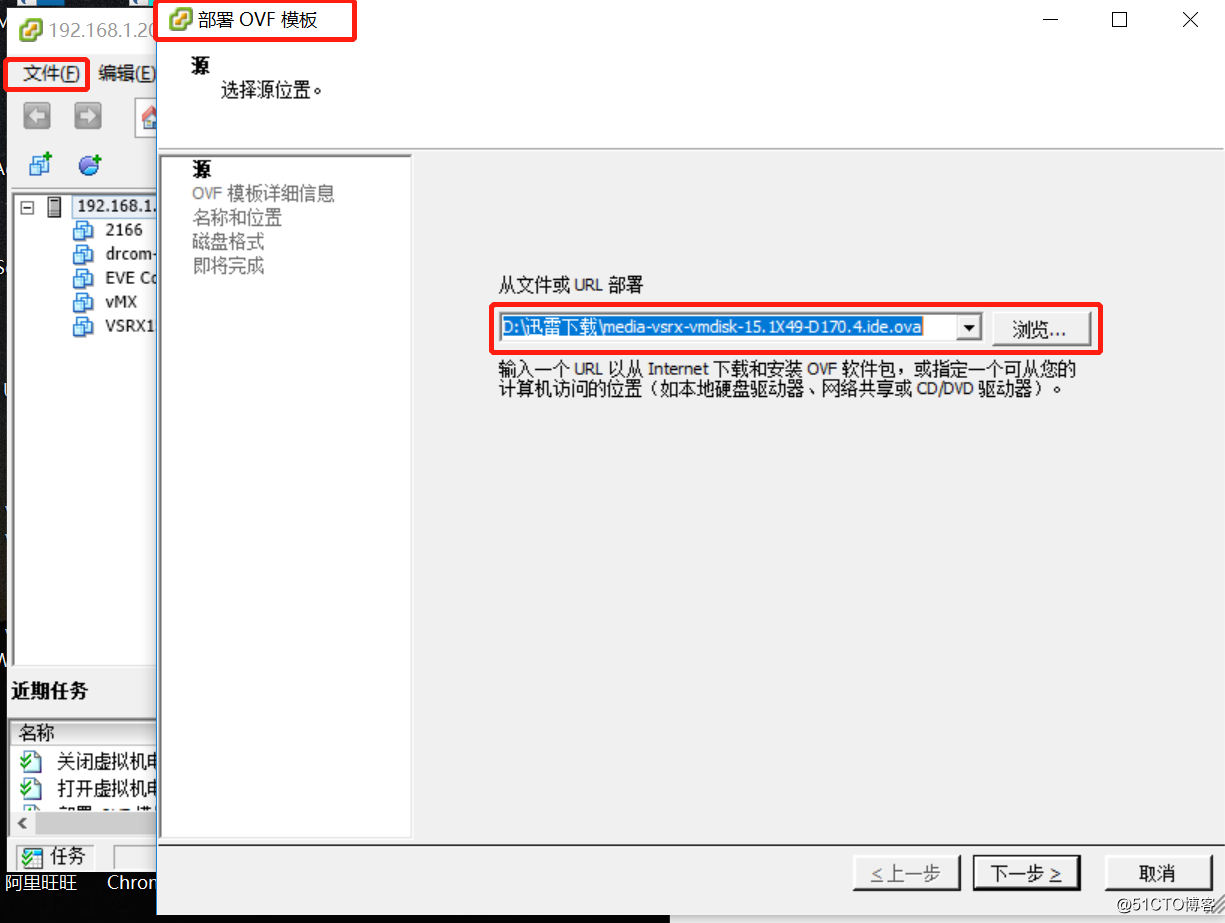
- 根据提示,点击完成
- 编辑虚拟机,设置相关参数
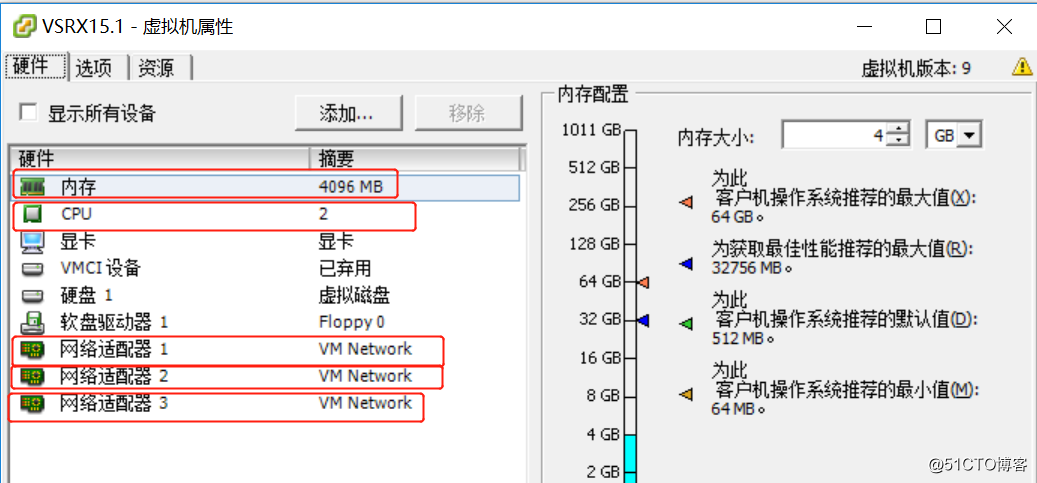
- 启动vsrx虚拟机,直至进入login界面
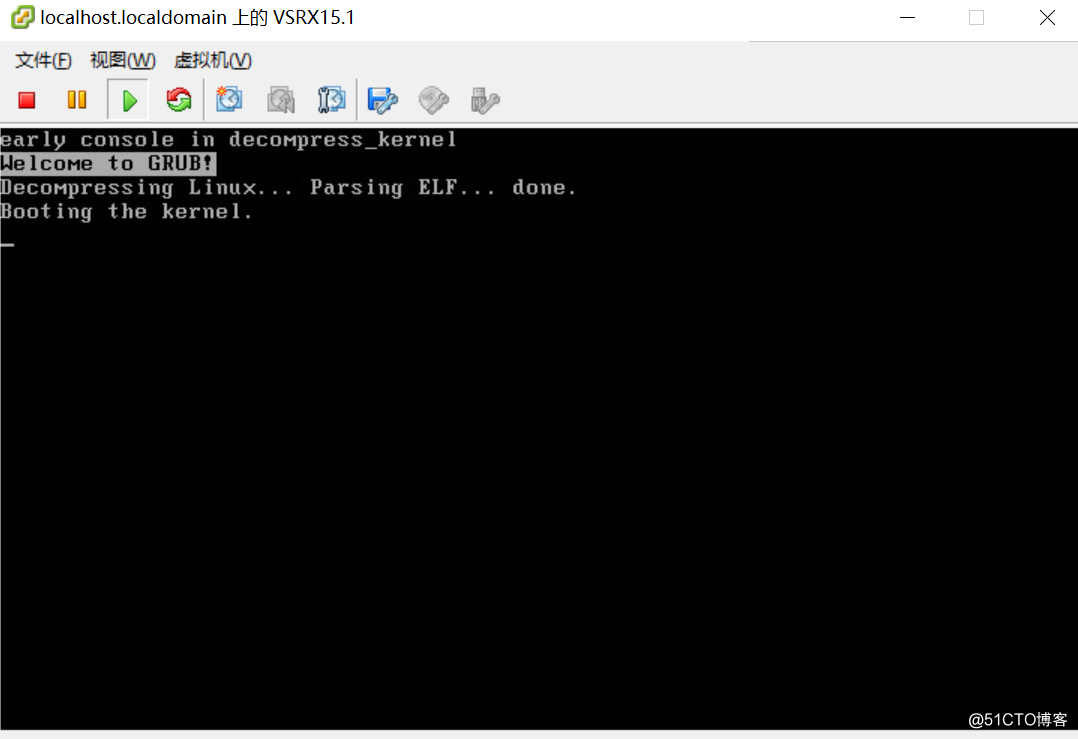
- 启动完成后,进入Login界面,用户名root,密码为空
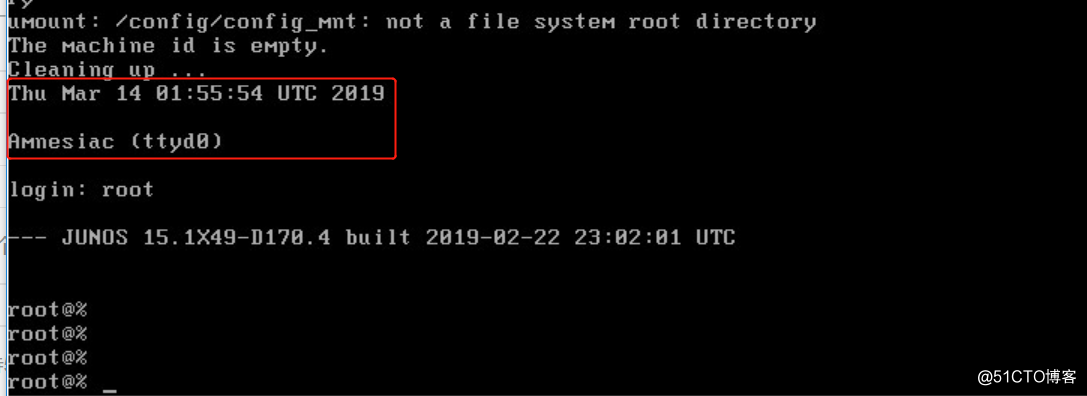
- 通过root用户名,直接进入shell界面,输入cli进入操作界面

- 从操作界面进入到配置界面,输入configuration
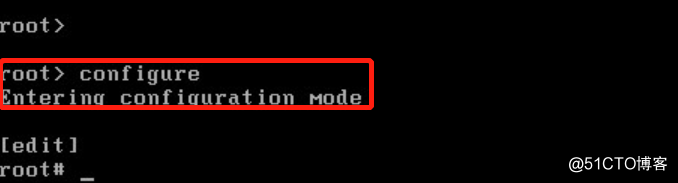
- 至此,vsrx换安装已经完成;
二、实验拓扑搭建
- 实现通过vmx、vsrx、isp链路组成逻辑拓扑图
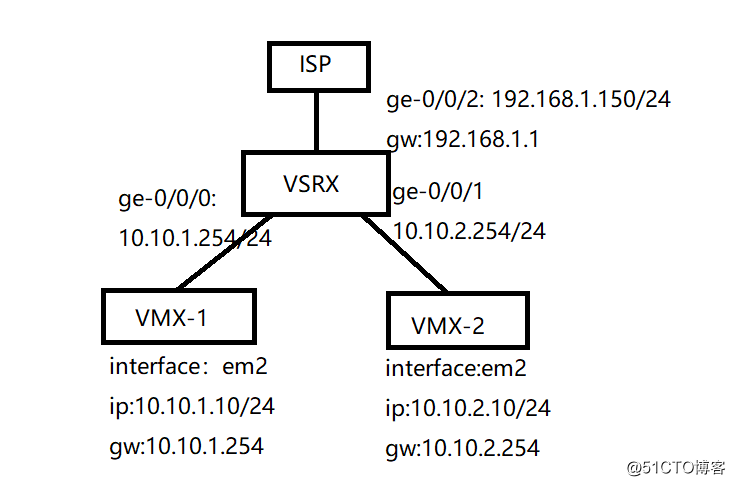
vmx-1网卡与vsrx ge-0/0/0在虚拟网卡vm2中
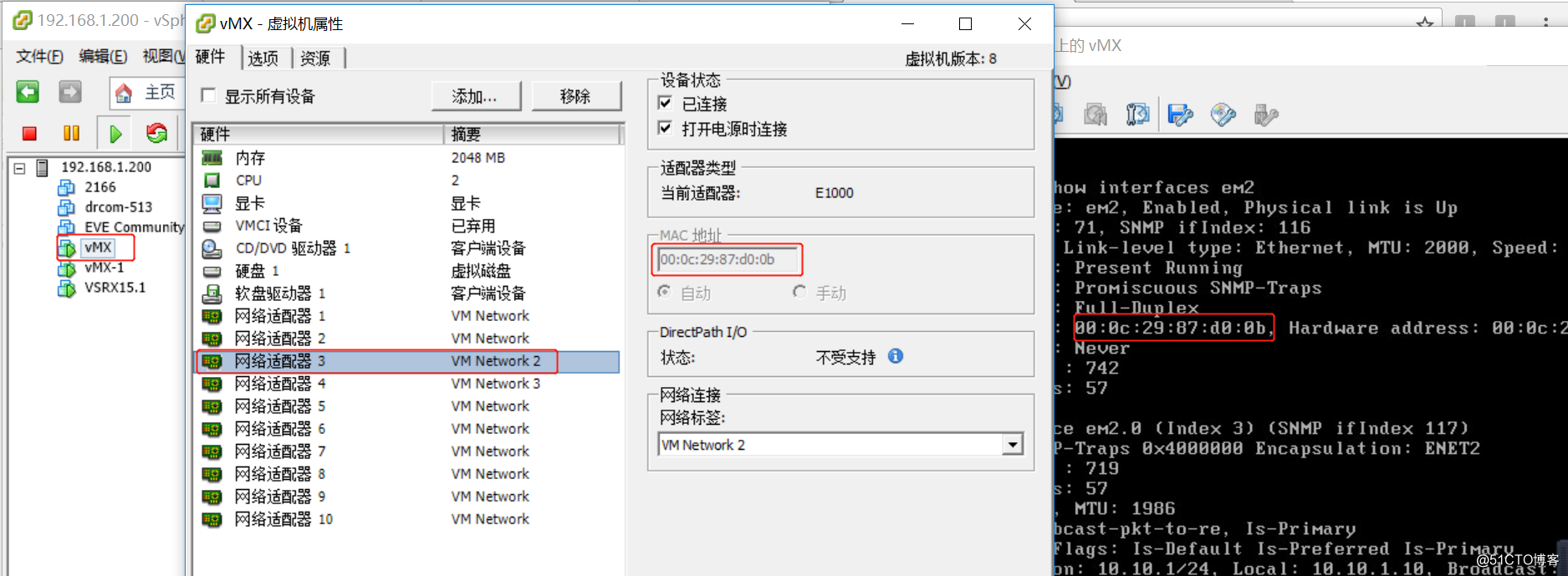 vmx-2网卡与vsrx ge-0/0/1在虚拟网卡vm3中
vmx-2网卡与vsrx ge-0/0/1在虚拟网卡vm3中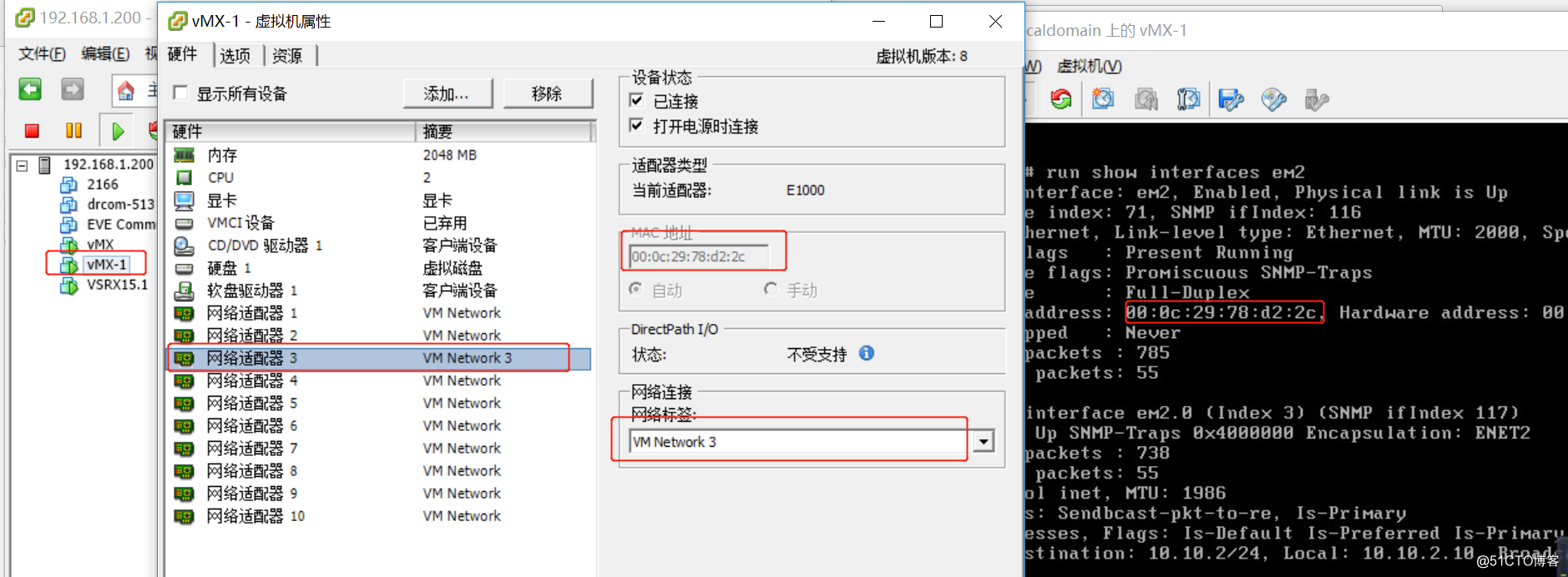 vsrx ge-0/0/0与isp在虚拟网卡vm中
vsrx ge-0/0/0与isp在虚拟网卡vm中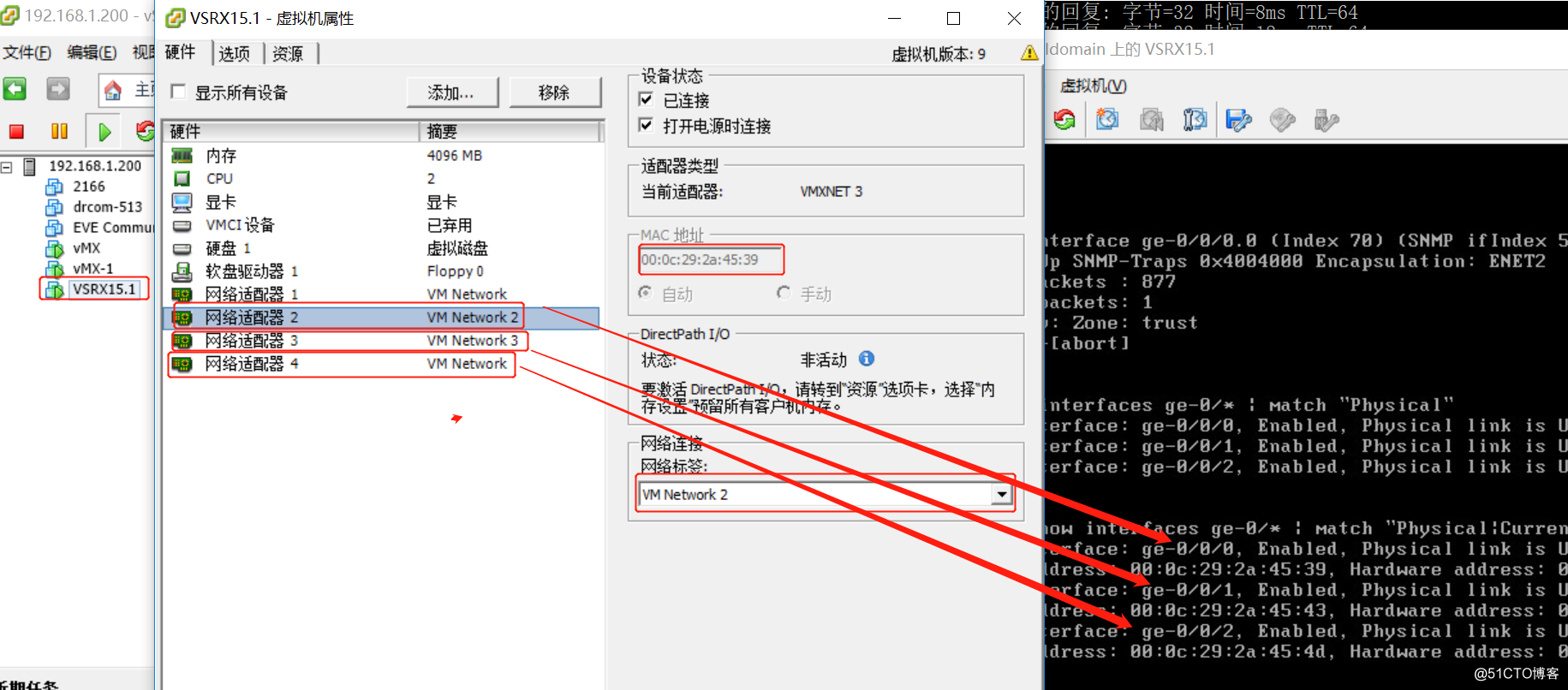
-
连通性测试:
vmx-1 ping vsrx ge-0/0/0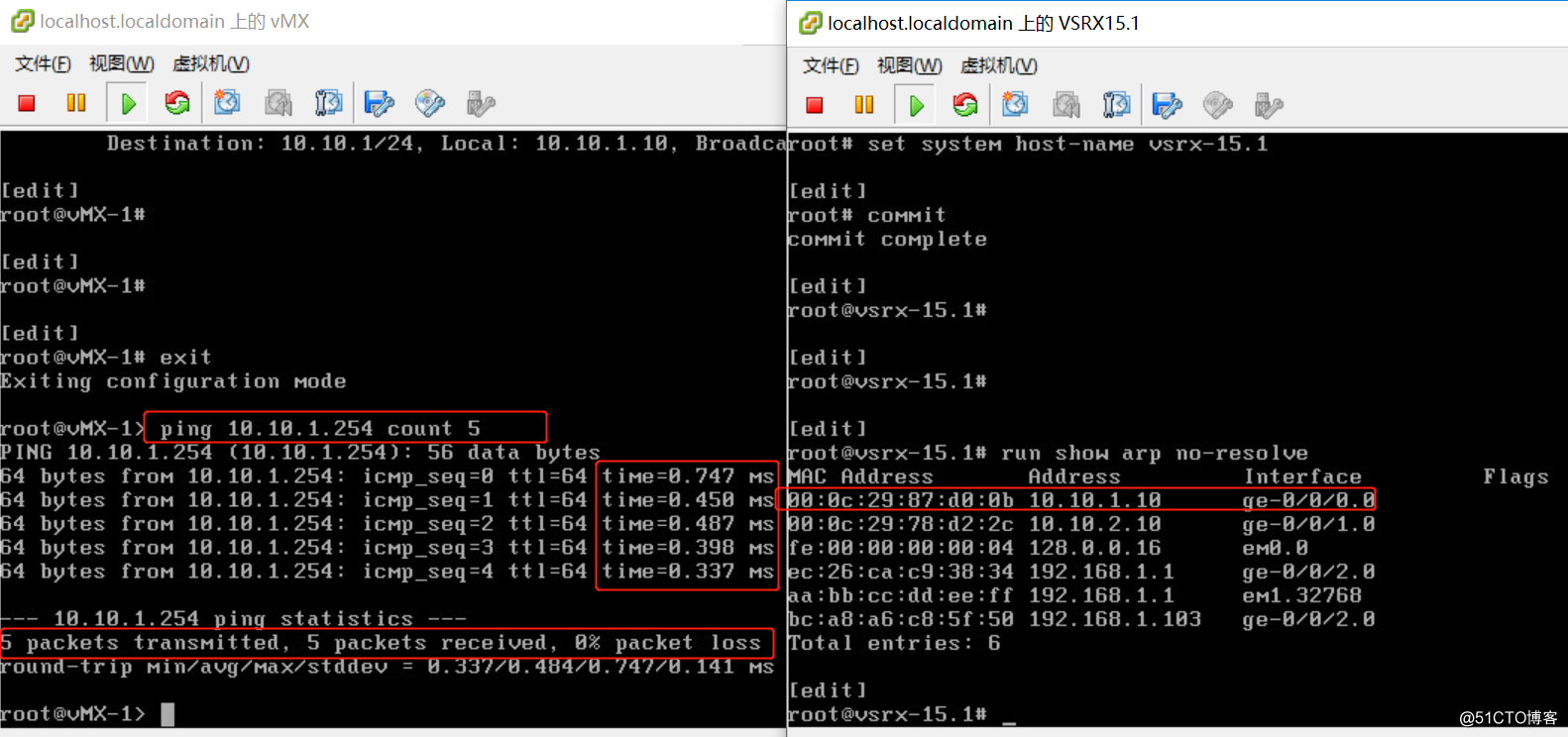 vmx-2 ping vsrx ge-0/0/1
vmx-2 ping vsrx ge-0/0/1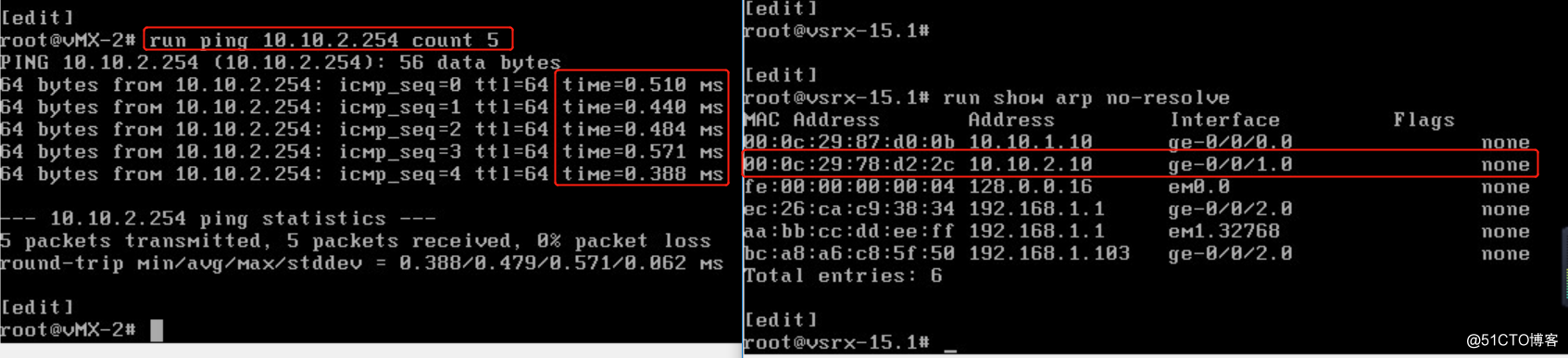 vsrx ge-0/0/2 ping isp 192.168.1.1, ping 114.114.114.114
vsrx ge-0/0/2 ping isp 192.168.1.1, ping 114.114.114.114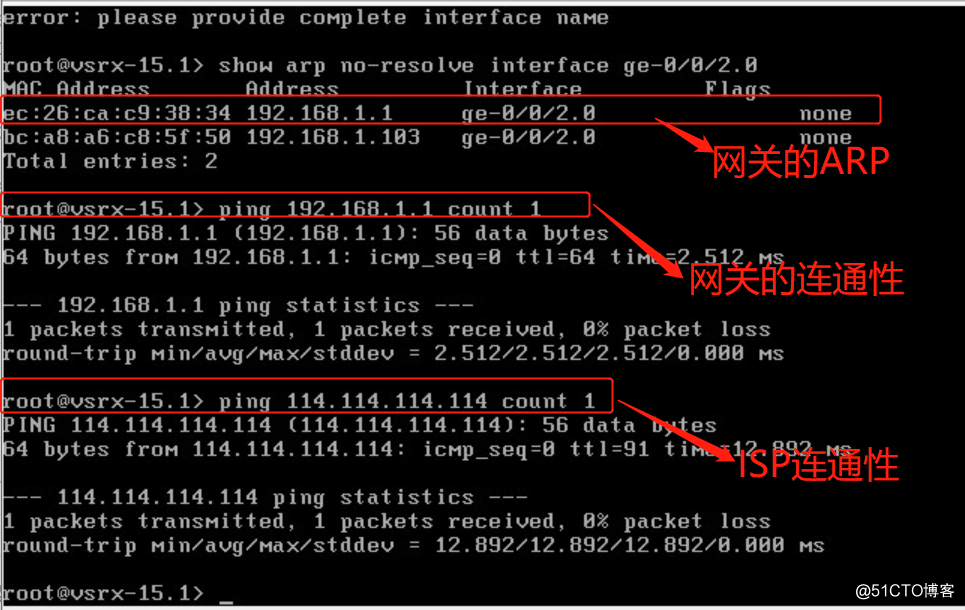
- vmx-1与vmx-2的连通性测试
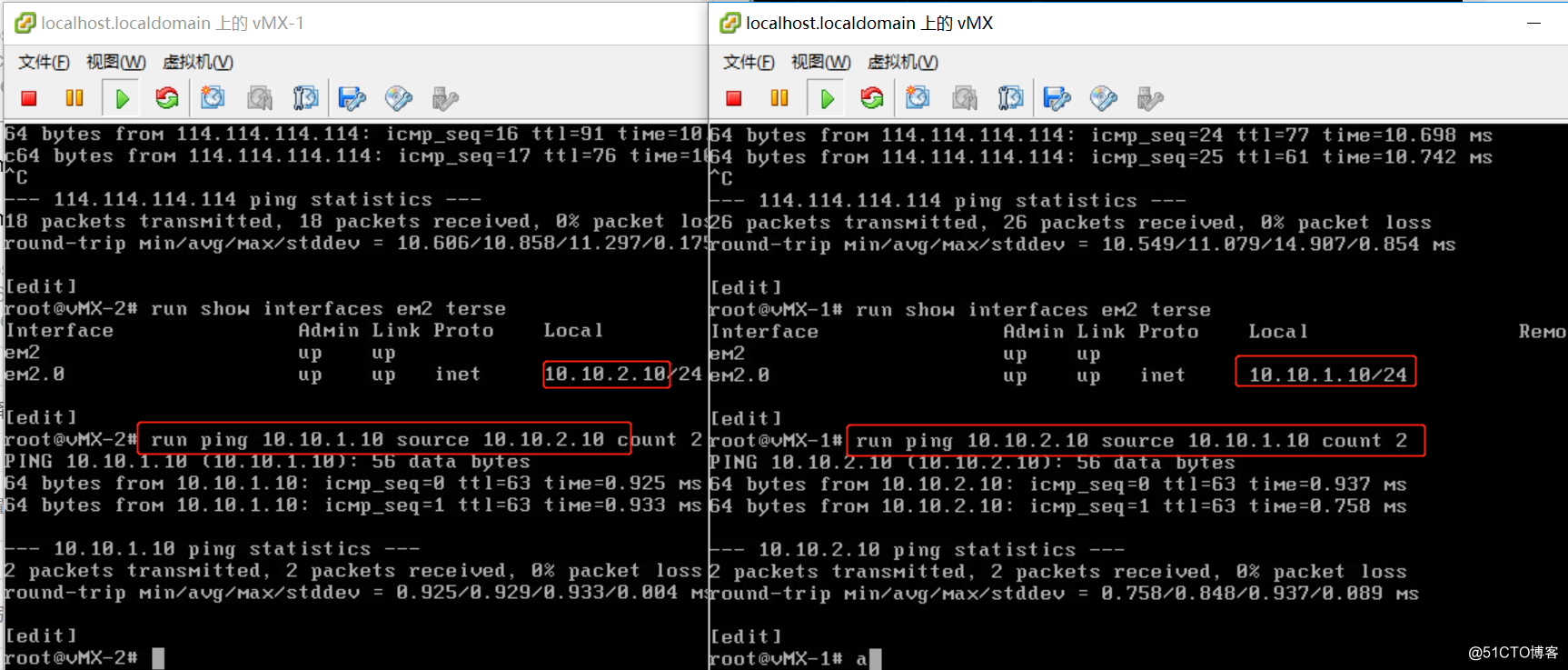
- vmx-1与vmx-2的Internet测试
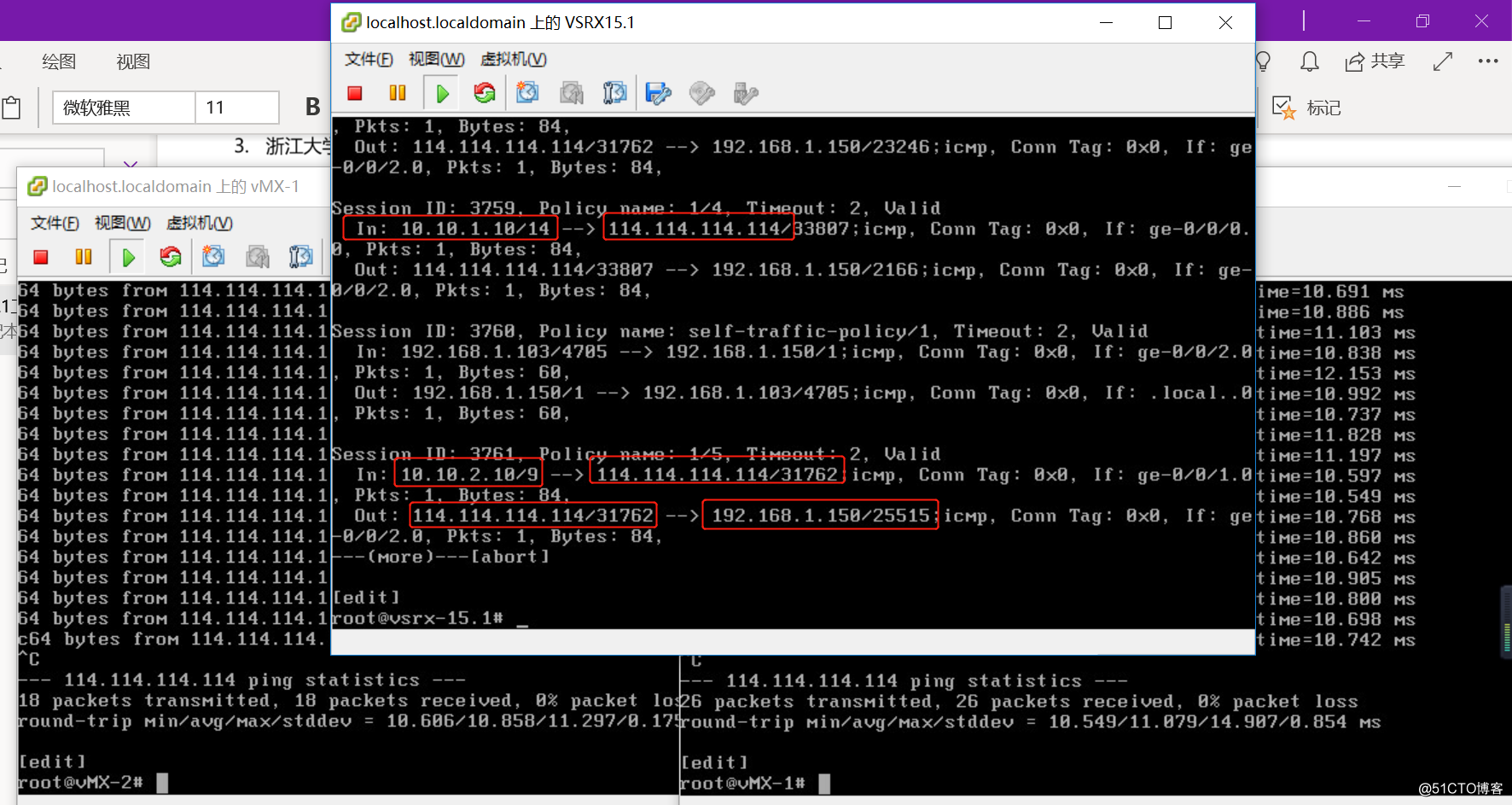
-
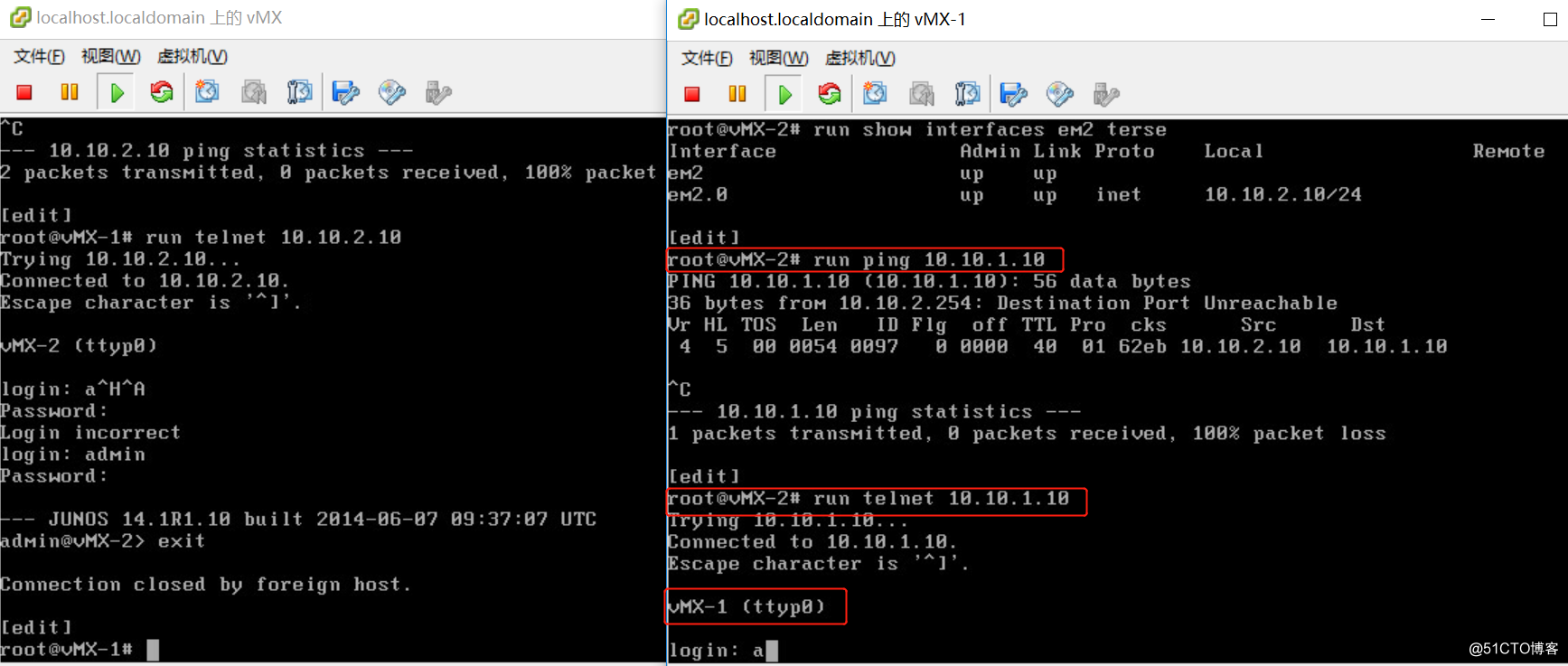
控制vmx-1和vmx-2的流量,不允许ping,ssh,只允许telnet。
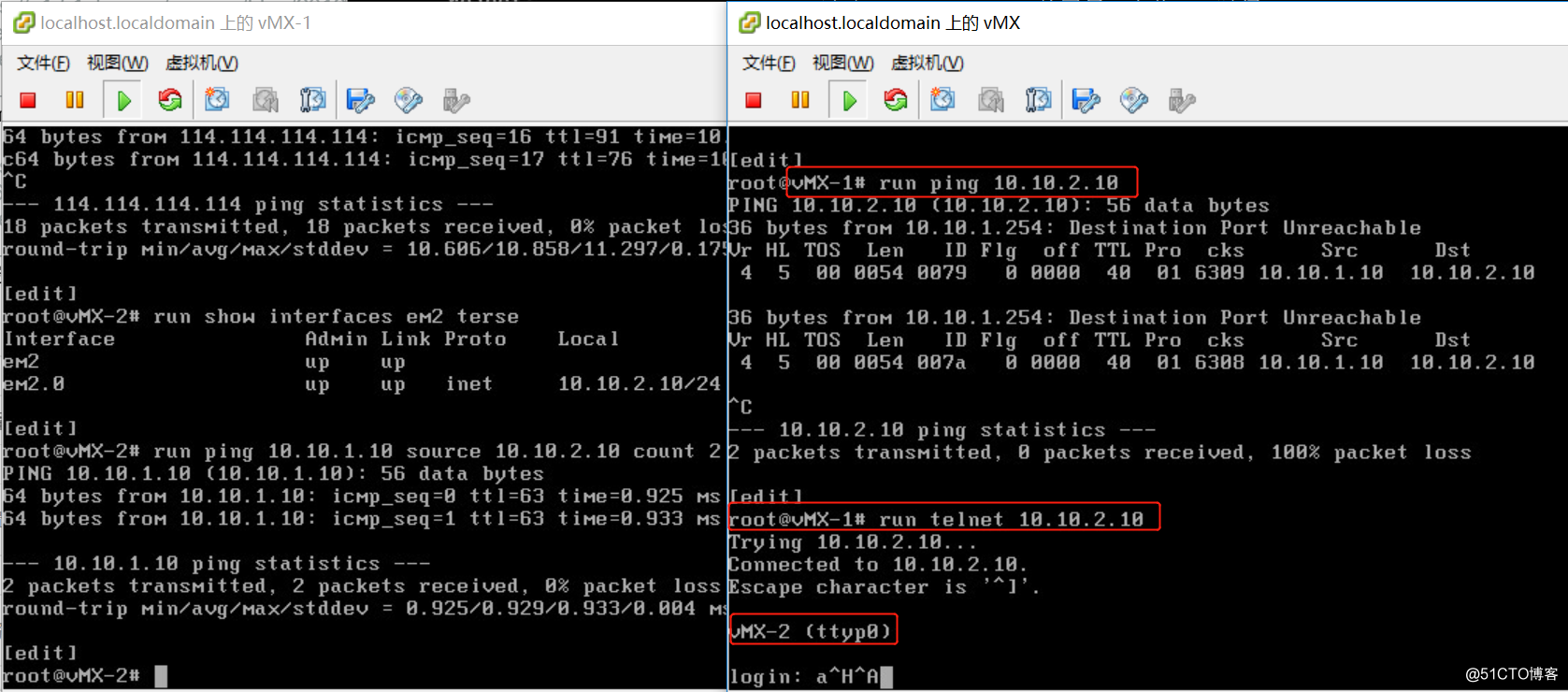
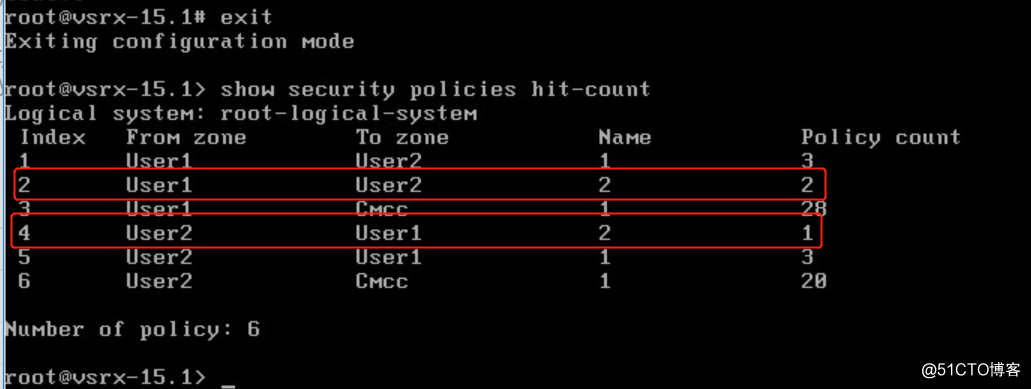
- 查看防火墙策略匹配的数量
总结:
以上为vsrx防火墙在vm中的部署步骤,注意vsrx网卡的桥接,vsrx防火墙使用的也是junos,操作方式和配置方式和物理防火墙一样,接触过srx防火墙,可以很快的上手vsrx。vSRX防火墙配置输出:
--- JUNOS 15.1X49-D170.4 built 2019-02-22 23:02:01 UTC
admin@vsrx-15.1> show configuration | no-more | display set set version 15.1X49-D170.4set system host-name vsrx-15.1set system root-authentication encrypted-password "$5$AUnhweol$AN5LIIlwt5sXB1OvLkrM7TpuCrAu/JLQqDmNfXuFZd5"set system name-server 8.8.8.8set system name-server 114.114.114.114set system login user admin uid 2000set system login user admin class super-userset system login user admin authentication encrypted-password "$5$ibd52KZv$NvtKlvBhZ3B5.5atZT0ipKRJ/BVqMruiO1lbY1PPsS4"set system services sshset system services telnetset system services web-management httpset system services web-management https system-generated-certificateset system syslog user * any emergencyset system syslog file messages any anyset system syslog file messages authorization infoset system syslog file policy_session user infoset system syslog file policy_session match RT_FLOWset system syslog file policy_session archive size 1000kset system syslog file policy_session archive world-readableset system syslog file policy_session structured-datadeactivate system syslog file policy_sessionset system syslog file event-log any anyset system syslog file event-log archive files 1set system syslog file event-log structured-dataset system license autoupdate url set security log mode eventset security address-book global address vmx-1 10.10.1.10/32set security address-book global address vmx-2 10.10.2.10/32set security screen ids-option untrust-screen icmp ping-deathset security screen ids-option untrust-screen ip source-route-optionset security screen ids-option untrust-screen ip tear-dropset security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048set security screen ids-option untrust-screen tcp syn-flood queue-size 2000set security screen ids-option untrust-screen tcp syn-flood timeout 20set security screen ids-option untrust-screen tcp landset security nat source rule-set snat from zone User1set security nat source rule-set snat from zone User2set security nat source rule-set snat to zone Cmccset security nat source rule-set snat rule 1 match source-address 10.10.1.0/24set security nat source rule-set snat rule 1 match source-address 10.10.2.0/24set security nat source rule-set snat rule 1 match destination-address 0.0.0.0/0set security nat source rule-set snat rule 1 then source-nat interfaceset security policies from-zone User1 to-zone Cmcc policy 1 match source-address anyset security policies from-zone User1 to-zone Cmcc policy 1 match destination-address anyset security policies from-zone User1 to-zone Cmcc policy 1 match application anyset security policies from-zone User1 to-zone Cmcc policy 1 then permitset security policies from-zone User2 to-zone Cmcc policy 1 match source-address anyset security policies from-zone User2 to-zone Cmcc policy 1 match destination-address anyset security policies from-zone User2 to-zone Cmcc policy 1 match application anyset security policies from-zone User2 to-zone Cmcc policy 1 then permitset security policies from-zone User1 to-zone User2 policy 2 match source-address vmx-1set security policies from-zone User1 to-zone User2 policy 2 match destination-address vmx-2set security policies from-zone User1 to-zone User2 policy 2 match application junos-icmp-pingset security policies from-zone User1 to-zone User2 policy 2 match application junos-sshset security policies from-zone User1 to-zone User2 policy 2 then rejectset security policies from-zone User1 to-zone User2 policy 2 then log session-initset security policies from-zone User1 to-zone User2 policy 2 then log session-closeset security policies from-zone User1 to-zone User2 policy 2 then countset security policies from-zone User1 to-zone User2 policy 1 match source-address anyset security policies from-zone User1 to-zone User2 policy 1 match destination-address anyset security policies from-zone User1 to-zone User2 policy 1 match application anyset security policies from-zone User1 to-zone User2 policy 1 then permitset security policies from-zone User2 to-zone User1 policy 2 match source-address vmx-2set security policies from-zone User2 to-zone User1 policy 2 match destination-address vmx-1set security policies from-zone User2 to-zone User1 policy 2 match application junos-icmp-pingset security policies from-zone User2 to-zone User1 policy 2 match application junos-sshset security policies from-zone User2 to-zone User1 policy 2 then rejectset security policies from-zone User2 to-zone User1 policy 2 then log session-initset security policies from-zone User2 to-zone User1 policy 2 then log session-closeset security policies from-zone User2 to-zone User1 policy 2 then countset security policies from-zone User2 to-zone User1 policy 1 match source-address anyset security policies from-zone User2 to-zone User1 policy 1 match destination-address anyset security policies from-zone User2 to-zone User1 policy 1 match application anyset security policies from-zone User2 to-zone User1 policy 1 then permitset security zones security-zone User1 interfaces ge-0/0/0.0 host-inbound-traffic system-services allset security zones security-zone User1 application-trackingset security zones security-zone User2 interfaces ge-0/0/1.0 host-inbound-traffic system-services allset security zones security-zone User2 application-trackingset security zones security-zone Cmcc interfaces ge-0/0/2.0 host-inbound-traffic system-services allset security zones security-zone Cmcc application-trackingset interfaces ge-0/0/0 unit 0 family inet address 10.10.1.254/24set interfaces ge-0/0/1 unit 0 family inet address 10.10.2.254/24set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.150/24set routing-options static route 0.0.0.0/0 next-hop 192.168.1.1vMX-1配置输出:
admin@vMX-1> show configuration | no-more | display set set version 14.1R1.10set system host-name vMX-1set system root-authentication encrypted-password "$1$wt0dI4la$d7JtEZv8MdB/aFx2Sf0cN."set system name-server 8.8.8.8set system login user admin uid 2001set system login user admin class super-userset system login user admin authentication encrypted-password "$1$ZndUPvaG$jUKRfxwDPyKgx8GJ5wJ0M/"set system services ftpset system services sshset system services telnet connection-limit 5set system syslog user * any emergencyset system syslog file messages any noticeset system syslog file messages authorization infoset system syslog file interactive-commands interactive-commands anyset interfaces em2 unit 0 family inet address 10.10.1.10/24set routing-options static route 0.0.0.0/0 next-hop 10.10.1.254vMX-2配置输出:
admin@vMX-2> show configuration | no-more | display set set version 14.1R1.10set system host-name vMX-2set system root-authentication encrypted-password "$1$A6hZKEhm$h/SdcxNgtaL0yN8NThxeu/"set system name-server 114.114.114.114set system login user admin uid 2001set system login user admin class super-userset system login user admin authentication encrypted-password "$1$HSS00OAL$KJx8HU4Ve6vTX9I.1SZWw/"set system services ftpset system services sshset system services telnet connection-limit 5set system syslog user * any emergencyset system syslog file messages any noticeset system syslog file messages authorization infoset system syslog file interactive-commands interactive-commands anyset interfaces em2 unit 0 family inet address 10.10.2.10/24set routing-options static route 0.0.0.0/0 next-hop 10.10.2.254转载于:https://blog.51cto.com/ciscosyh/2362862
你可能感兴趣的文章
嵌入式开发培训都要学什么?零基础参加嵌入式学习培训能学会吗
查看>>
flume的初体验
查看>>
hbase的基本操作
查看>>
DevOps工程师到底做些什么?
查看>>
解析RDD在Spark中的地位
查看>>
高质量SEO文章编辑规范技巧之:格式
查看>>
Liunx磁盘存储和文件系统
查看>>
人工智能在4S店、网店,应用经验分享
查看>>
linux下清空mysql密码
查看>>
Oracle 11g r2数据泵新特性(五)
查看>>
oracle技术之Rman备份恢复命令
查看>>
COBBLER无人值守安装
查看>>
解决golang.org/x包无法下载的问题
查看>>
ansible puppet saltstack三款自动化运维工具的对比
查看>>
PHP - windows下编译PHP 7.1的memcache
查看>>
手机互动网页项目总结(转)
查看>>
SAPCAR简单使用
查看>>
shell脚本每天自动备份mysql数据库
查看>>
TeamViewer 局域网 远程桌面
查看>>
Spring4学习笔记-Spring4整合Hibernate4
查看>>